It seems like almost every week there is a new type of malware or ransomware making headlines, threatening our online security and bringing an organization to its knees. The stolen funds, hard drive encryption, theft of confidential corporate information and bad publicity are front page news. Cyber criminals are becoming smarter and using innovative techniques to get into someone’s computer and access valuable data.
Given the evolution of information technology, almost every organization is adopting or migrating to emerging technologies, such as cloud, social and mobile computing, to interconnect their different offices for exchanging information and conducting business online. This has not only increased their online presence but also their exposure to security threats and cyber crime. Cyber criminals are not only targeting businesses but individuals too. Nowadays everyone is connected to the internet almost all the time either through wireless or mobile data and thus no one is immune to cyber threats. And after so many cyber criminal incidents, I must say that antivirus alone is not enough to protect your PC from such malicious viruses, malware or ransomware. So the big question is “How can you protect yourself or your organization from cyber threats?”
As attackers employ advanced innovative techniques and exploit security vulnerabilities, you must keep yourself up to date with the latest developments and research on cyber threats to avoid becoming a victim of cyber crime. If you are running a small business or working as an IT professional for an organization, you must also adopt strict cyber security measures in order to respond to these increased threats and protect your business or company from any types of cyber threats such as hacking, virus attacks, spyware, malware, or ransomware attacks, etc. Here are some cyber security basics that everyone should be aware of.
How do you protect yourself from cyber threats and avoid becoming a victim of cyber crime?
#1. Keep your software up to date
#2. Use a good Antivirus program and keep it up to date
#3. Use a Good firewall and Internet Security Suite
Now the question is “how many of such software solutions do you need?” and “are they effective enough to provide you with full security and keep you completely safe online?” and, most importantly, “are they proactive enough to fight against the current evolving and emerging security threats?”
After reviewing multiple antiviruses and internet security suites, I stumbled upon one of the best security software named Heimdal which is unique in its type as it does not only block incoming attacks, ransomware, banking trojans, phishing attempts, but also updates or patches third party applications in order to close vulnerabilities and mitigate exploits. Most importantly, its professional version, Heimdal PRO, doesn’t rely on analyzing the malware’s code or its behavior like antiviruses do. It uses advanced traffic monitoring and filtering technologies to protect your PC from any types of malicious content and security threats. Before we move further, let me explain how Heimdal is different from other internet security products. Also just to check its effectiveness we also installed it on our system and ran several security checks and it passed them all, so we rate it 5 out of 5. Read this review to understand how effective an internet security software should be.
 |
| Heimdal PRO Review |
What is Heimdal ?
1. Heimdal Free
Features :
- Keeps your vulnerable third party apps up to date automatically, in the background (silently, without any user interruption).
- Resolves critical security vulnerabilities in your software.
- Provides one-click safe install for new Apps.
- Comes with a Very Simple interface that anyone can use.
- Free technical support.
Features:
- Advanced Internet Traffic Scanning and Filtering
- Traffic-based Malware Detection
- Online Banking Security
- Robust protection against: Malware, Adware & Spyware, Ransomware, Botnets, Browser & DNS hijacking, Email Spam and Malware Distribution, Exploit Kits, Fileless Malware, Keyloggers, Macro Viruses, Malicious Traffic Redirects, Malvertising, Phishing, Whaling, Pharming, Potentially unwanted programs (PUPs), Remote Access Trojans , Rogueware, URL & SQL injection, Zero Day Malware.
3. Heimdal CORP
Why Heimdal?
How to install Heimdal and how effective is it?
The installation and setup of Heimdal PRO is very simple. You just need to download the installer from the official website. Click here to download Heimdal PRO free for 30 days. The installer named Heimdal.DeliveryLauncher.msi is just 756 KB in size.
1. When you run the installer, it downloads the rest of the installation and setup files, which are around 34 MB in size. It is available in three different languages: English, Danish and German. During installation it also checks if your PC already has Microsoft .NET Framework 4.6.1 and downloads it from Microsoft’s server if not found.
 |
| Heimdal PRO Installation |
2. Select the custom install location or leave it default as C:Program Files (x86)Heimdal and click next.
3. Choose to activate a free 30-day trial if you do not have a license key, or select the second option “I want to activate Heimdal PRO/CORP” if you have a license key. Type the license key and click Activate.
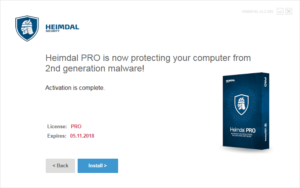 |
| Heimdal PRO Review |
4. Click the install button once it is activated successfully.
5. Now it will ask you to configure the product, which is pretty straightforward. Or you can leave it as default and simply click next to complete the set up.
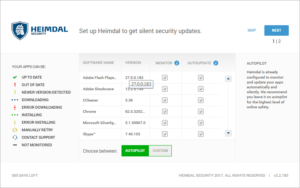 |
| Heimdal PRO Setup-1 |
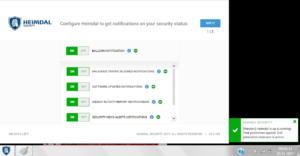 | |
|
6. Now after the setup is complete, it will show the status of your system and, if it’s the case, a message that your computer must be updated. Once it has scanned your system and updated your vulnerable software, it will display a message in green, confirming that your computer is healthy.
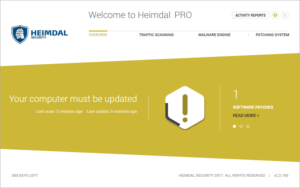 |
| Critical Message about the system |
 |
| Healthy System Status |
7. Heimdal comes with a very simple interface that anyone can understand, split into Overview, Traffic Scanning, Malware Engine and Patching System. First, click on the Traffic Scanning tab.
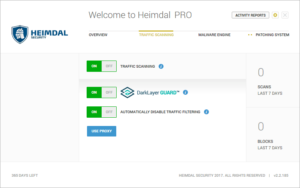 |
| Heimdal PRO – Traffic Scanning |
8. The “DarkLayer GUARD” in traffic scanning checks whether the domains your computer connects to are harmful by looking into Heimdal’s database of known Malicious domains. Just to check this feature, I tried to visit some harmful websites and Heimdal PRO blocked them, displaying the following message:
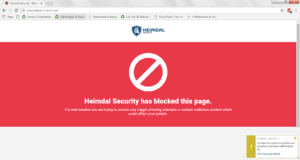 |
| Website Blocked by Heimdal PRO’s DarkLayer GUARD |
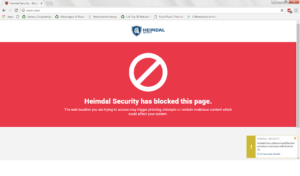 |
| Harmful Website Blocked by Heimdal PRO’s DarkLayer GUARD |
9. The second tab, Malware Engine, allows you to turn Malware scanning on or off. The VectorN Detection feature analyzes your internet traffic and blocks known, newly discovered, or unknown malware, by detecting internet communication patterns in your internet traffic.
 |
| Heimdal PRO – Malware Engine |
10. The third interface “Patching System” shows you the list of outdated apps and their status whether they have been updated and patched or not. It also shows you the list of some recommended apps based on their popularity.
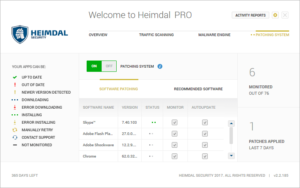 |
| Heimdal PRO – Patching System |
11. Apart from the easy to manage interface, it also has an activity report section where it shows various useful information about Heimdal PRO’s activity during the last 7 days. The general tab in Activity Reports shows the number of scanned and blocked domains, the number of scans made by the Malware Engine and the VectorN detections, the number of software apps it monitors and the number of patches applied in the last 7 days.
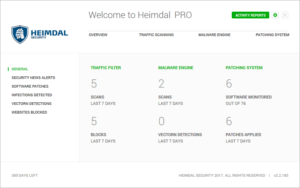 |
| Heimdal PRO Activity Report |
12. Under the General tab, you can go into more detailed reports by clicking on Software Patches, Infections Detected, VectorN Detections, or Websites Blocked.
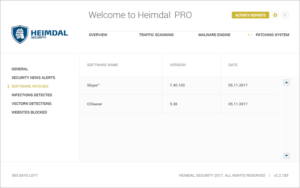 |
| Software Patches Report |
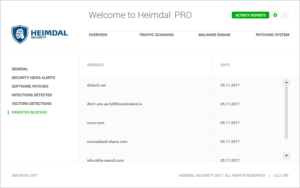 |
| Report of Harmful Websites Blocked by Heimdal PRO |
So if you are looking for an effective and powerful internet security software, I recommend giving Heimdal PRO a try, as it is lightweight and available at a very reasonable price with so many rare features.
Now let’s get back to the basics of cyber security and the practices we should follow to prevent our PC and data from cyber attacks. Apart from the above mentioned major steps and the software installation, you should also do the following.
#4. Use unique and strong passwords for each website, change your default password as soon as possible
#5. Enable two-factor authentication wherever available
#6. Avoid connecting USB flash drives or hard drives you don’t trust to your computer.
#7. Carefully read the message and permissions while installing a new app and don’t just keep clicking on the next button.
#8. Don’t send or upload sensitive personal data via email or cloud sharing, if necessary, do encrypt it in a zip file before sending or uploading it.
#9. Make sure the website is secure by looking at the padlock sign in the address bar before entering your personal or financial information.
#10. Avoid using or logging into your main accounts on public computers or while connected to a free shared Wi-Fi network.
#11. Regularly back up your important files to avoid losing them
#12. Review your social media security settings and security questions. Change them immediately if you suspect someone knows them.
#13. Most importantly, keep yourself always updated with the latest trends, development and research in the field of cyber security, as it gives you important information on how to avoid being a victim of new emerging threats and what precaution you should take. Almost all major software manufacturers keep updating their blog with such incidents, causes and remedies. Heimdal ‘s security alerts section on their blog is one of such places where you can find the latest information on hot researched topics and breaking news about new threats and their evolution. You can also subscribe to their blog to be the first to know and stop cyber attacks.