Amazon S3 Express One Zone Now Supports Server-Side Encryption with AWS Key Management Service (KMS) Keys
Amazon has recently announced an exciting update for its S3 Express One Zone storage class. This high-performance, single-Availability Zone (AZ) storage class now supports server-side encryption using AWS Key Management Service (KMS) keys (SSE-KMS). Previously, S3 Express One Zone already provided encryption for all objects stored in S3 directory buckets using Amazon S3 managed keys (SSE-S3) by default. However, with the new update, users can now leverage AWS KMS customer-managed keys for data encryption at rest without any negative impact on performance.
The addition of this encryption capability provides users with an extra layer of security, helping to meet compliance and regulatory requirements. S3 Express One Zone is specifically designed to deliver consistent, single-digit millisecond data access, making it ideal for frequently accessed data and latency-sensitive applications.
Understanding S3 Directory Buckets and Key Management
When using S3 directory buckets, you can specify only one customer-managed key per bucket for SSE-KMS encryption. Once you add a customer-managed key, you cannot change it to a new key. In contrast, S3 general-purpose buckets allow the use of multiple KMS keys either by changing the default encryption configuration of the bucket or during S3 PUT requests.
With S3 Express One Zone, S3 Bucket Keys are always enabled when using SSE-KMS. S3 Bucket Keys are free and significantly reduce the number of requests to AWS KMS by up to 99%, optimizing both performance and costs.
Using SSE-KMS with Amazon S3 Express One Zone
To demonstrate this new feature, let’s consider the process of creating an S3 directory bucket in the Amazon S3 console. Here are the steps:
- Creating an S3 Directory Bucket:
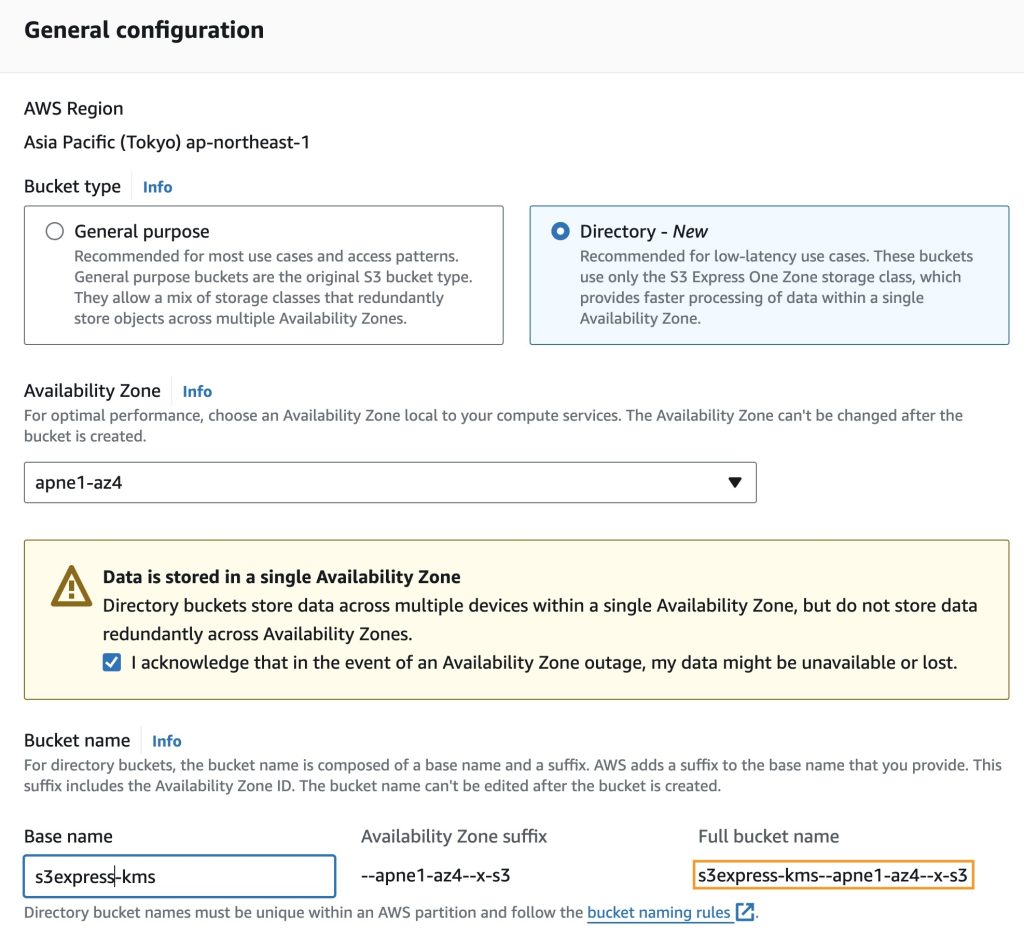
- In the Amazon S3 console, follow the steps to create an S3 directory bucket and use
apne1-az4as the Availability Zone. - Enter
s3express-kmsas the base name along with a suffix that includes the Availability Zone ID, which is automatically added to create the final name. - Select the checkbox to acknowledge that data is stored in a single Availability Zone.

- In the Amazon S3 console, follow the steps to create an S3 directory bucket and use
- Setting Default Encryption:
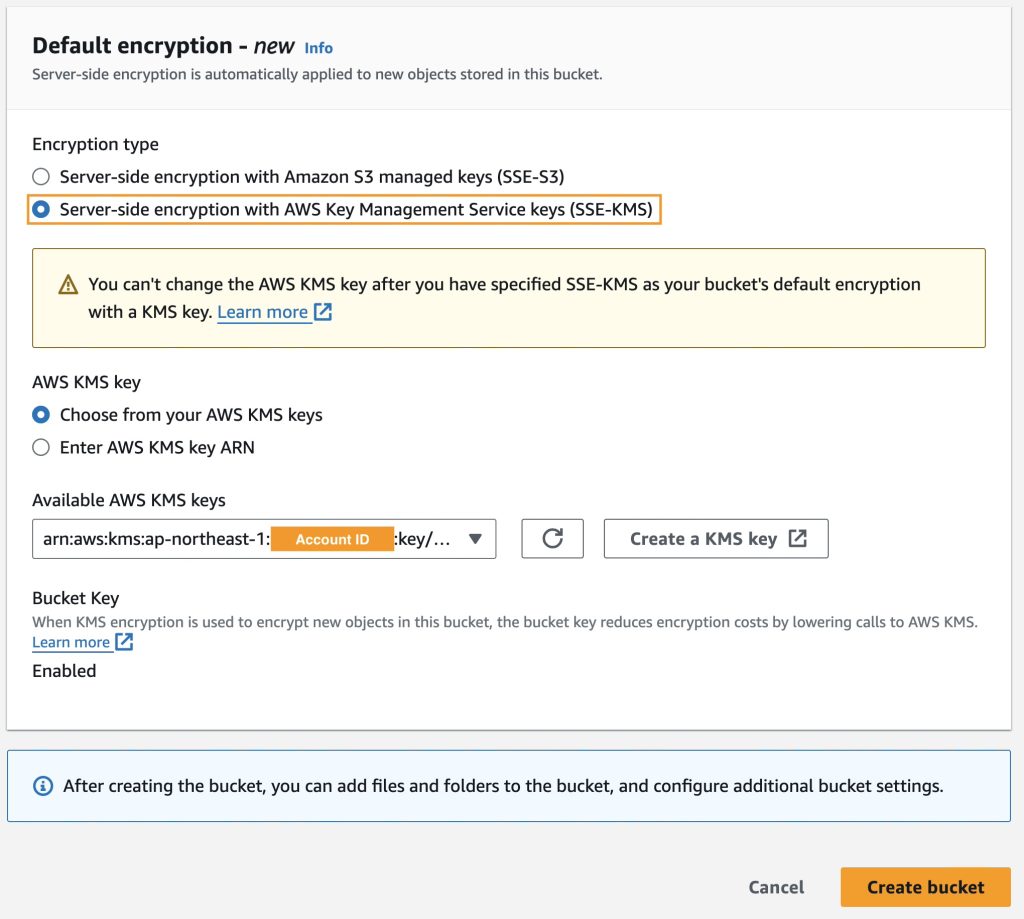
- In the Default Encryption section, choose Server-side encryption with AWS Key Management Service keys (SSE-KMS).
- Under AWS KMS Key, you can choose from your AWS KMS keys, enter the AWS KMS key ARN, or create a new KMS key.
- For this example, a previously created AWS KMS key is selected from the list, and then the bucket is created.

Now, any new object uploaded to this S3 directory bucket will be automatically encrypted using the selected AWS KMS key.
SSE-KMS with Amazon S3 Express One Zone in Action
To use SSE-KMS with S3 Express One Zone via the AWS Command Line Interface (CLI), you need an AWS Identity and Access Management (IAM) user or role with the following policy. This policy allows theCreateSession APIoperation, which is necessary to successfully upload and download encrypted files to and from your S3 directory bucket.
json<br /> {<br /> "Version": "2012-10-17",<br /> "Statement": [<br /> {<br /> "Effect": "Allow",<br /> "Action": [<br /> "s3express:CreateSession"<br /> ],<br /> "Resource": [<br /> "arn:aws:s3express:*:<account>:bucket/s3express-kms--apne1-az4--x-s3"<br /> ]<br /> },<br /> {<br /> "Effect": "Allow",<br /> "Action": [<br /> "kms:Decrypt",<br /> "kms:GenerateDataKey"<br /> ],<br /> "Resource": [<br /> "arn:aws:kms:*:<account>:key/<keyId>"<br /> ]<br /> }<br /> ]<br /> }<br />
Uploading a File
Using thePutObjectcommand, you can upload a new file namedconfidential-doc.txtto your S3 directory bucket.
sh<br /> aws s3api put-object --bucket s3express-kms--apne1-az4--x-s3 \<br /> --key confidential-doc.txt \<br /> --body confidential-doc.txt<br />
Upon successful execution, you receive the following output:
json<br /> {<br /> "ETag": "\"664469eeb92c4218bbdcf92ca559d03b\"",<br /> "ChecksumCRC32": "0duteA==",<br /> "ServerSideEncryption": "aws:kms",<br /> "SSEKMSKeyId": "arn:aws:kms:ap-northeast-1:<accountId>:key/<keyId>",<br /> "BucketKeyEnabled": true<br /> }<br />
Checking the Object’s Properties
To check the object’s properties, use theHeadObjectcommand. This confirms that the object is encrypted using SSE-KMS with the specified key.
sh<br /> aws s3api head-object --bucket s3express-kms--apne1-az4--x-s3 \<br /> --key confidential-doc.txt<br />
The output would be:
json<br /> {<br /> "AcceptRanges": "bytes",<br /> "LastModified": "2024-08-21T15:29:22+00:00",<br /> "ContentLength": 5,<br /> "ETag": "\"664469eeb92c4218bbdcf92ca559d03b\"",<br /> "ContentType": "binary/octet-stream",<br /> "ServerSideEncryption": "aws:kms",<br /> "Metadata": {},<br /> "SSEKMSKeyId": "arn:aws:kms:ap-northeast-1:<accountId>:key/<keyId>",<br /> "BucketKeyEnabled": true,<br /> "StorageClass": "EXPRESS_ONEZONE"<br /> }<br />
Downloading the Encrypted Object
To download the encrypted object, use theGetObjectcommand:
sh<br /> aws s3api get-object --bucket s3express-kms--apne1-az4--x-s3 \<br /> --key confidential-doc.txt output-confidential-doc.txt<br />
If your session has the necessary permissions, the object will be downloaded and decrypted automatically.
json<br /> {<br /> "AcceptRanges": "bytes",<br /> "LastModified": "2024-08-21T15:29:22+00:00",<br /> "ContentLength": 5,<br /> "ETag": "\"664469eeb92c4218bbdcf92ca559d03b\"",<br /> "ContentType": "binary/octet-stream",<br /> "ServerSideEncryption": "aws:kms",<br /> "Metadata": {},<br /> "SSEKMSKeyId": "arn:aws:kms:ap-northeast-1:<accountId>:key/<keyId>",<br /> "BucketKeyEnabled": true,<br /> "StorageClass": "EXPRESS_ONEZONE"<br /> }<br />
Testing Access Permissions
For a second test, use a different IAM user with a policy that does not grant the necessary KMS key permissions to download the object. This attempt should fail with anAccessDeniederror, demonstrating that the SSE-KMS encryption is functioning as intended.
sh<br /> An error occurred (AccessDenied) when calling the CreateSession operation: Access Denied<br />
Things to Know
Getting Started
You can enable SSE-KMS for S3 Express One Zone using the Amazon S3 console, AWS CLI, or AWS SDKs. Set the default encryption configuration of your S3 directory bucket to SSE-KMS and specify your AWS KMS key. Remember that you can only use one customer-managed key per S3 directory bucket for its lifetime.
Regions
S3 Express One Zone support for SSE-KMS using customer-managed keys is available in all AWS Regions where S3 Express One Zone is currently available.
Performance
Using SSE-KMS with S3 Express One Zone does not impact request latency. You will continue to experience the same single-digit millisecond data access.
Pricing
You will incur AWS KMS charges to generate and retrieve data keys used for encryption and decryption. For more details, visit the AWS KMS pricing page. Additionally, when using SSE-KMS with S3 Express One Zone, S3 Bucket Keys are enabled by default for all data plane operations except forCopyObjectandUploadPartCopy, and cannot be disabled. This reduces the number of requests to AWS KMS by up to 99%, optimizing both performance and costs.
AWS CloudTrail Integration
You can audit SSE-KMS actions on S3 Express One Zone objects using AWS CloudTrail. For more information, refer to a previous blog post on monitoring data events in Amazon S3 Express One Zone with AWS CloudTrail.
For more details, you can visit the official AWS Polly page.
By leveraging these features, users can ensure their data is secure while maintaining optimal performance and compliance with regulatory requirements.
- In the Default Encryption section, choose Server-side encryption with AWS Key Management Service keys (SSE-KMS).